
In 2023, several SIM swap attacks have targeted cryptocurrency advocates and high-profile industry members, including Ethereum co-founder Vitalik Buterin. Below is a comprehensive guide aimed at educating our readers on mitigating SIM swap attacks and safeguarding against hacks.
Understanding the Threat: Unmasking SIM Swap Attacks
Recently, Bitcoin.com News reported that Ethereum co-founder Vitalik Buterin fell victim to a SIM swap attack. Moreover, this week, an Ethereum (ETH) investor suffered a SIM swap attack, losing 22 ETH on the friend.tech blockchain social media platform, which operates on the Base network. Unfortunately, a significant number of SIM swap attacks are targeting crypto investors. The subsequent walkthrough will guide our readers on how to avert a SIM swap attack.
So, what is a SIM swap attack? A SIM swap attack is a type of fraud in which a malicious actor deceives a mobile carrier into transferring the victim’s phone number to a new SIM card controlled by the attacker. Once the phone number is transferred, the attacker can receive the victim’s calls and text messages, including sensitive authentication codes sent via SMS for two-factor authentication (2FA).
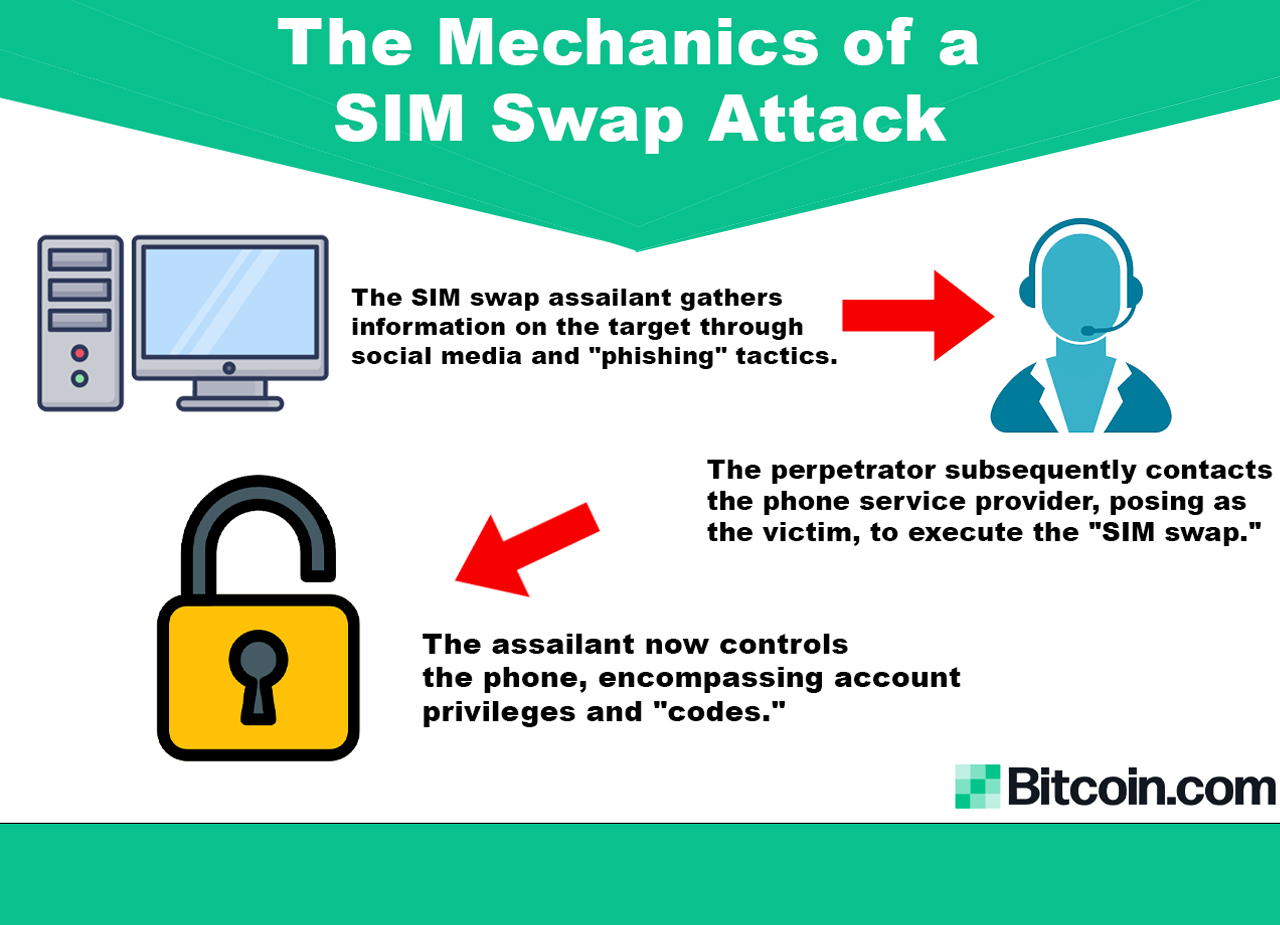
This breach enables the attacker to bypass security measures and gain unauthorized access to the victim’s online accounts, such as email, crypto exchange accounts, and social media profiles, leading to potential financial loss and identity theft. While mitigation efforts are never 100% effective, there are several strategies individuals can employ to combat SIM swap breaches.
First Line of Defense: Online Vigilance; Password and Authentication Strategies
The first step is essentially online vigilance by being cautious of phishing emails and other tactics used by attackers to gain access to your personal information. Further enhanced vigilance includes avoiding responses to suspicious communications such as unknown texts, emails, and phone calls. The second measure is to leverage strong and unique passwords that protect each online account. Third, the use of two-factor authentication (2FA) is recommended, and veering away from an SMS text message or email-based 2FA is also advisable. It’s wise to use stronger multi-factor authentication (MFA) methods such as standalone authentication applications, biometrics, or physical security keys.
Engaging Your Mobile Carrier: Security Enhancements; Guarding Social Media, Online Platforms
Another protective method, and one of the most important, is to engage in security measures by contacting your telephone carrier. With specific carriers, you can request additional security measures on your account. Users can also establish a unique PIN or passcode with their carrier, which adds an extra layer of security. Some telephone line carriers offer SIM protection features that add extra security to prevent SIM swap fraud. If you don’t contact your telephone carrier, you may miss out on some of the security measures that could prevent a SIM swap attack.
Another measure is to avoid using your telephone number for social media applications like X (formerly Twitter) and other online platforms and applications. Alongside your phone number, be cautious about sharing personal information online as every piece of evidence a hacker can gather is useful to crack online accounts. For services that require a phone number for verification or communication, consider using a secondary number or a virtual phone number service like Google Voice.
By following these steps, you can avoid a SIM swap attack and protect your finances and personal information. SIM-swapping attacks have been increasing in frequency in recent years, and the U.S. Federal Bureau of Investigation (FBI) issued a warning in March 2023 about the rise of SIM-swapping attacks, which have resulted in millions of dollars in losses.
Have you taken steps to protect yourself from SIM swap attacks? Let us know your strategies in the comments section below.
Comments
Post a Comment